How Mature Is Your Cybersecurity Management - 1
Cyber Security Capability Maturity Model
What is a Capability Maturity Model
A maturity model is a framework that helps organizations assess and improve their capabilities and practices in a specific area, such as technology, cybersecurity, or project management. It typically consists of different levels or stages that represent varying degrees of proficiency or maturity.
When an an organization progresses through these levels, it demonstrates increasing competence and effectiveness in that area. SSimply put Maturity models serve as roadmaps for organizations to enhance their capability and reach higher levels of proficiency.
In the context of cybersecurity, a maturity model helps organizations evaluate and enhance their cybersecurity practices. It provides a structured way to assess an organization’s readiness and effectiveness in protecting its digital assets from threats and risks.
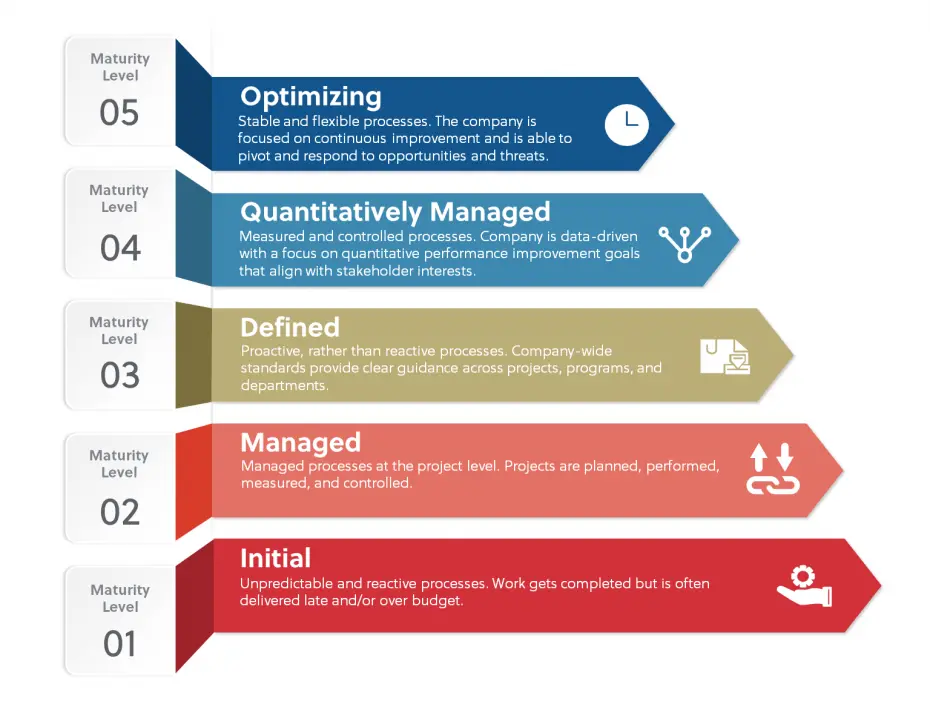
While there are many different Cybersecurity maturity models, I find these levels to be most reliable and better named,
- Level 0 – Not Assessed
- This level of maturity is defined as “non-existence practices,” where the controls are not being performed and practices are informal, inconsistent, and reactive
- Level 1 – Initiated
- This level of maturity is defined as “Level 1 - Initiated” where the controls are being performed, but lacks completeness & consistency.
- Level 2 – Defined
- This level of maturity is defined as “Level 2 - Defined” where the controls in place however are not standardized across relevant bodies. Controls are project or objective driven.
- Level 3 – Managed
- This level of maturity is defined as “Level 3 - Managed” where the controls in place, well planned and standardized across relevant bodies. Controls are in place as a precautionary measure and deviances are justified.
- Level 4 – Mature and Capable
- This level of maturity is defined as “Level 4 - Mature” where the controls in place, well defined, standardized across relevant bodies. Controls are data driven to provide quantitative understating of capability, and its effects.
- Level 5 – Enhanced
- This level of maturity is defined as “Level 5 - Enhanced” where the controls in place, well defined, planned, standardized and is continuously improving with metrics and up to date world/industry practices. The goal is effective and efficient controls.
By using these stages, organizations can identify their current level of cybersecurity maturity and create a roadmap for progressing to higher levels.
This essentially helps them strengthen their security posture.
How does it work?
First thing to know is that you need some form of a tool for this, most organizations simply use a huge Excel but I have seen some applications as well.
Step 0 - Domains
Before actually staring off you have to decide on the scope and the domains. What are you trying you asses? All domains of Cyber Security that your company works in or a smaller portion of it.
Depending on what you are aiming for or why you started this Assessment, there many different domains you either create custom domains and figure ot the requirements and levels yourself or you can use existing frameworks set domains, requirements and levels.
Here are some examples for these domains.
- Asset and Change Management
- Asset information with critical defined -configuration baselines for assets -Review logs of changes to assets
- Risk Management
- Assessing and managing cybersecurity risks, including identifying vulnerabilities and threats, and developing strategies to mitigate risks.
- Access Control
- Managing and controlling access to systems and data, including user authentication, authorization, and data protection.
- Physical Security
- Providing a safe and secure physical environment for your people, information, and assets.
- Security Governance
- Establishing governance structures and responsibilities for cybersecurity, often involving senior management and board oversight.
- Legislation
- Might be needed for in highly regulated industries like finance, healthcare, telecom and government organizations.Legal requirements and industry regulations is a critical aspect of cybersecurity for many such organizations.
- Management structure, roles, and responsibilities
- About how you allocate and support human resources to achieve your security objectives.
- Security Monitoring
- Implementing tools and processes to continuously monitor systems and networks for suspicious or malicious activities.
- Incident Response
- Developing and implementing procedures for detecting, responding to, and recovering from cybersecurity incidents and breaches.
- Security Culture and behaviors:
- Educating employees and stakeholders about cybersecurity best practices and promoting a security-conscious culture within the organization.
As you can see there are many possible domains and you can add or subtract more domains depending on your needs.
After you decided on your domains the next step is to either figure out the what requirements would one need for each level of maturity in that domain.
For a very brief and easy example on requirements.
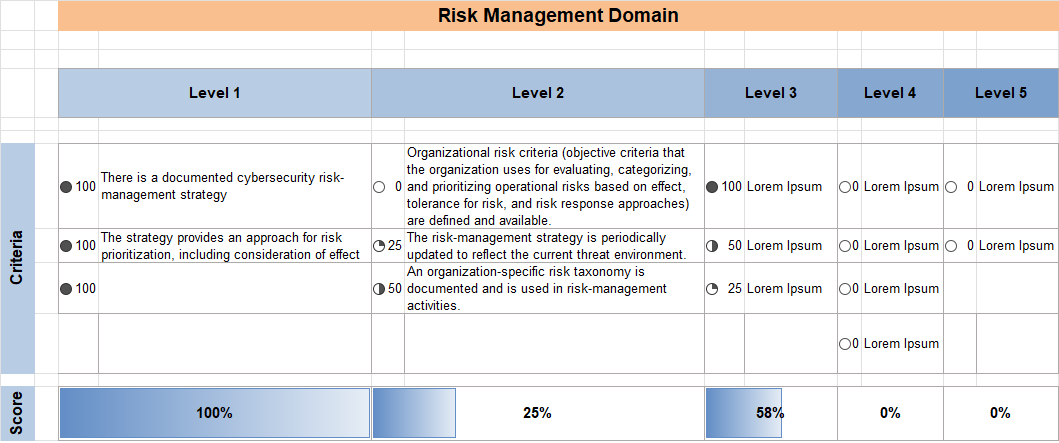 Super Basic Risk Management Requirements and Levels
Super Basic Risk Management Requirements and Levels
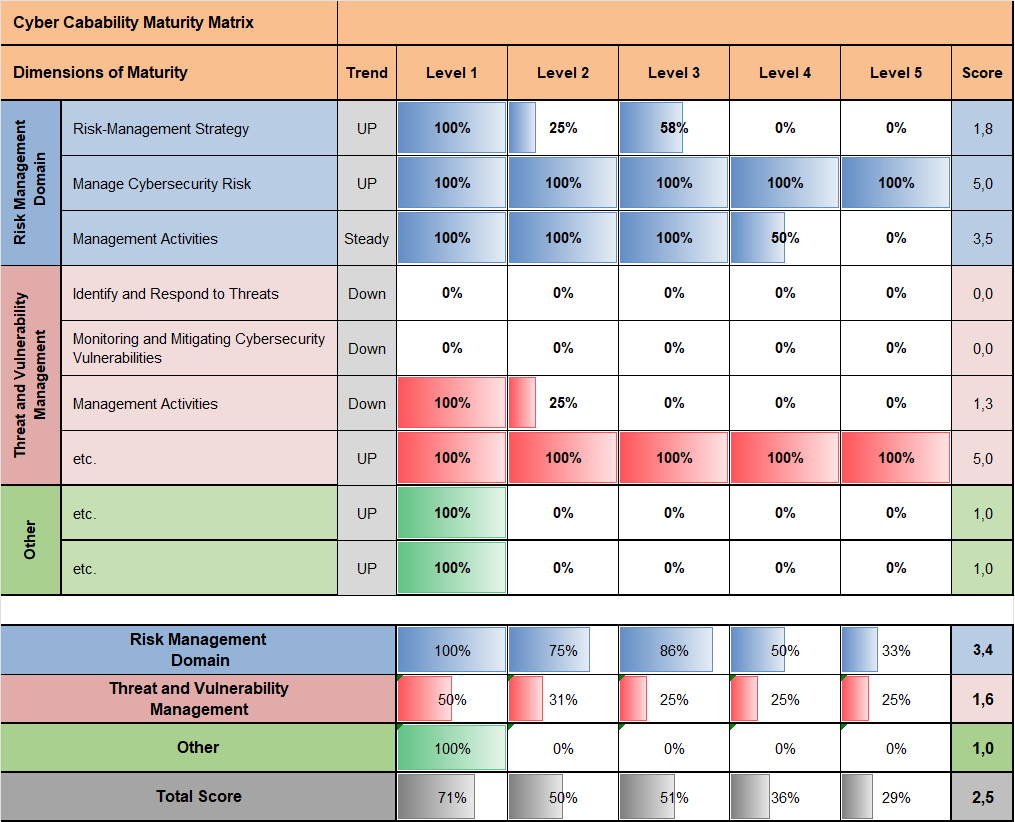
After regiments and levels are set for each domain you have chosen in very simple terms most of your work is finished as excel tools will generate a matrix similar to the one below.
With this you have an high level over view on you organizations Cyber Security Capability Maturity Model. What do you need to do after this?
Well I’ll talk about in the next part. I’m planning to talk about the steps and how to proceed after domains and requirements are set.